AppSec In Datadog For DevSecOps
Based on all of the AI-generated code that's positioned to run in production, Application Security (AppSec) is becoming what general cybersecurity was 10 years ago - the default. The reason why is due to the speed of AI-generated code, humans are almost on autopilot and not thinking about the implications of the generated code in production. Because of that, we need a method for testing every code base in an efficient manner prior to deployment (enter DevSecOps).
In this blog post, you'll learn about measures to not only scan code, but ensure that even after post deployment, it's secure in production.
Prerequites
To follow along from a hands-on perspective in this blog post, you'll need a Datadog account. So you don't have to pay for one, you can get a 14-day free trial here.
What Is AppSec/DevSecOps
The security conversation usually goes something like this.
Security Person: Hey, this thingy isn't secure.
Engineer:
- It's going to take forever to secure it
- It'll make us go slower
- We can't innovate
- We need those libraries
Manager: We need to worry about features and customers, not security. Security doesn't pay the bills.
All of the above happens in some capacity (I obviously oversimplified it) and all of it is true at the same time. Things need to be secure, but features need to go out. Security folks need to be hired, but the company needs to hire another backend Dev to implement the new feature that customers need.
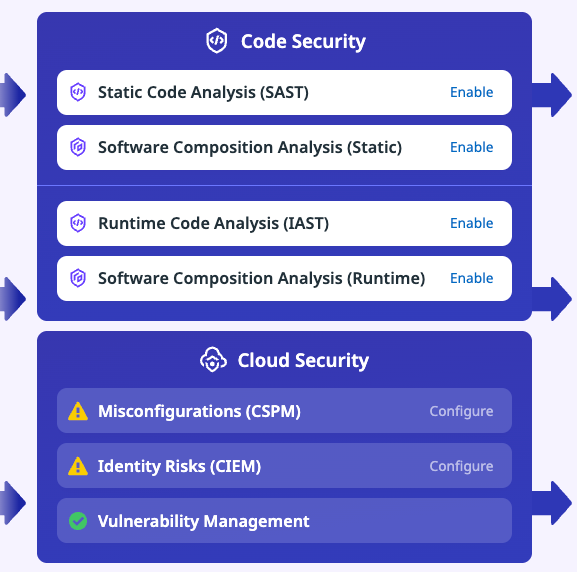
The idea of DevSecOps and AppSec is to remediate all concerns while still keeping things secure. For example, in the same pipeline that a new feature is getting built and containerized within the CI process (along with all of the other testing that occurs like unit tests and integration tests), a Static Application Security Testing (SAST) can occur. The results can then be sent to whichever AppSec/DevSecOps tool you're using, which an engineer on the security team can then pick up and hopefully remediate.
Tldr; AppSec and DevSecOps shouldn't slow down velocity. It'll just catch issues that engineers otherwise wouldn't have known existed.
Enabling SAST In Datadog
Now that you know a bit about the "why" behind DevSecOps and AppSec, let's see it in action.
For the hands-on portion of this blog post, you'll learn how to set up the entire configuration for SAST within Datadog.
- Log into Datadog and go to the Security pane.
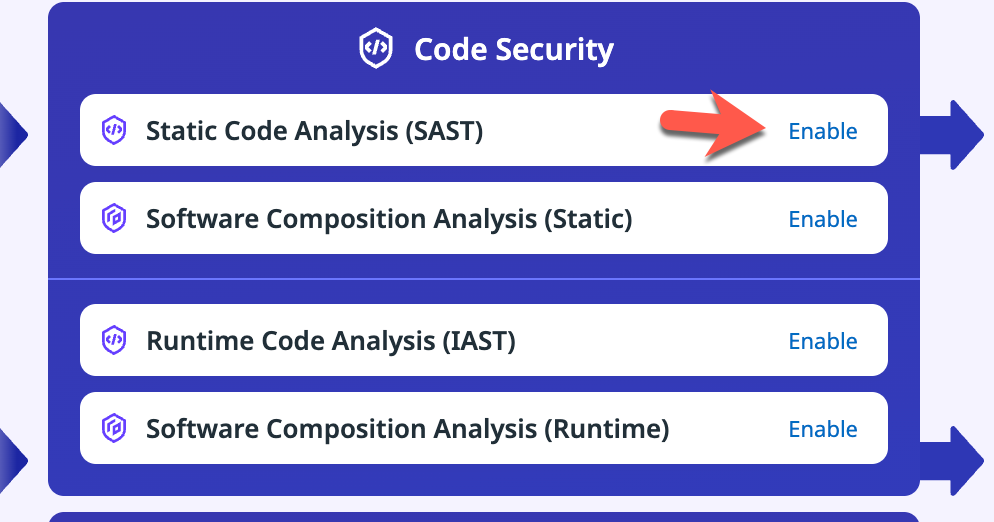
- Click the blue Enable button next to Static Code Analysis (SAST).
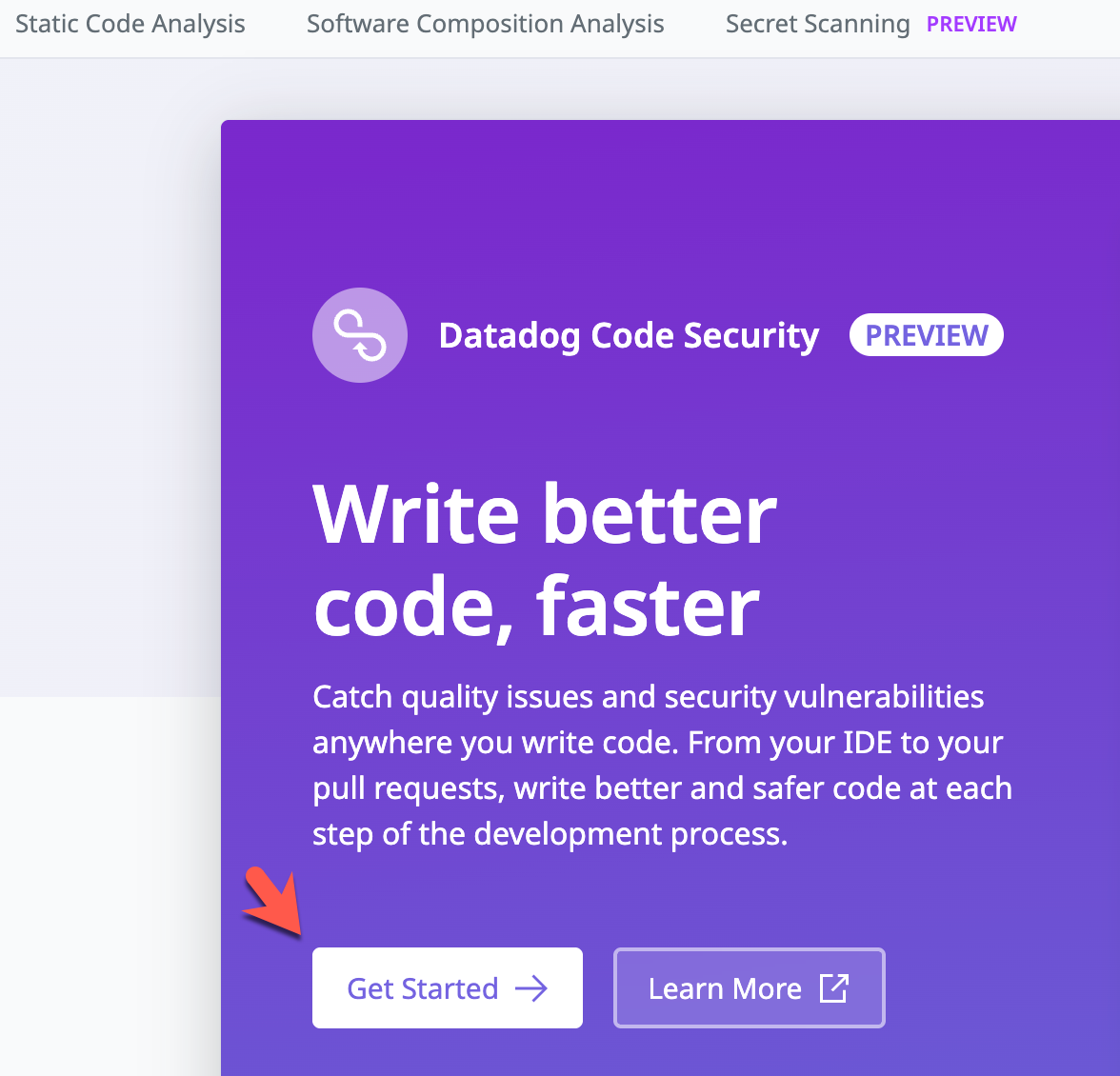
- Click the Get Started -> button.
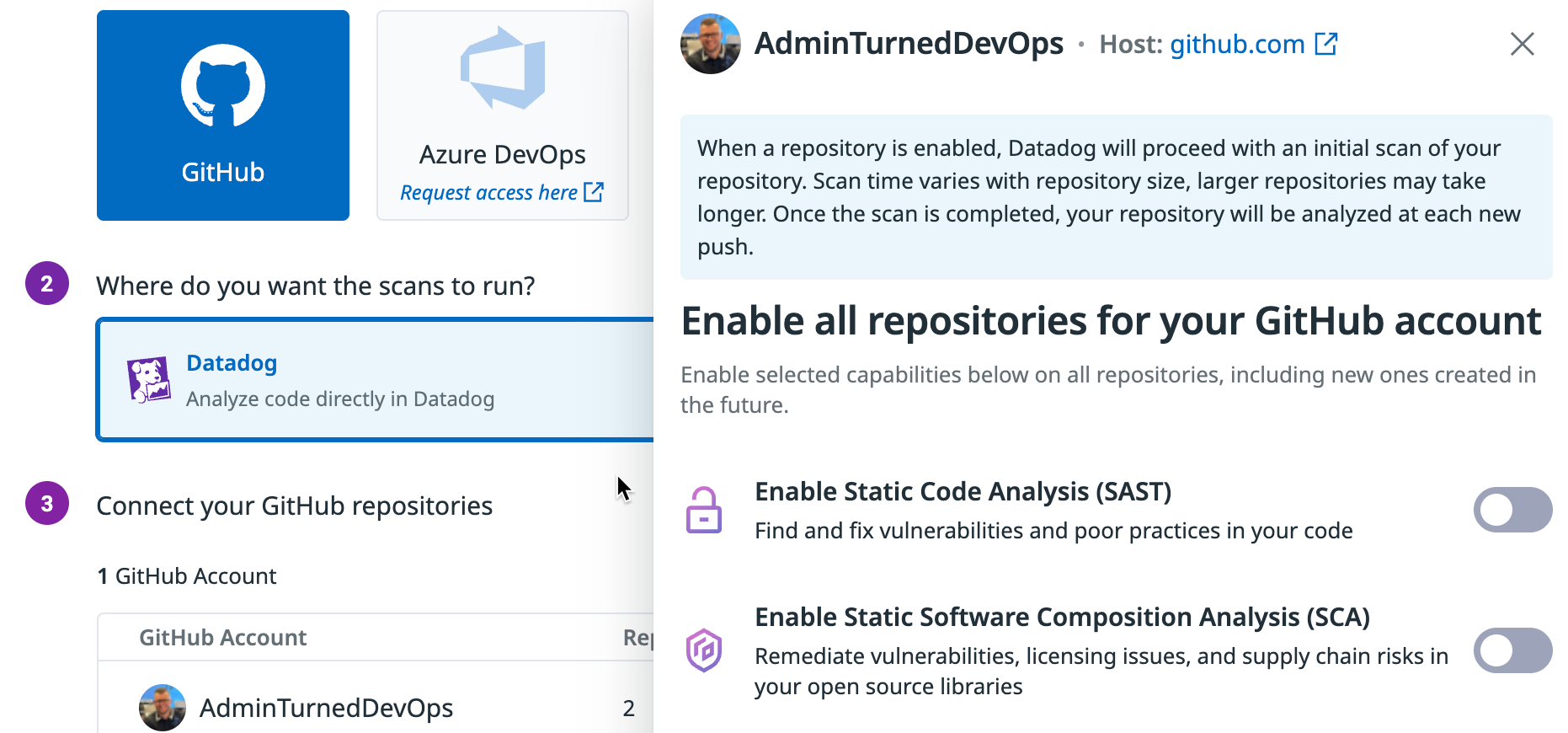
- Choose GitHub (or another repo you're using) and use Datadog for where the scans will be run.
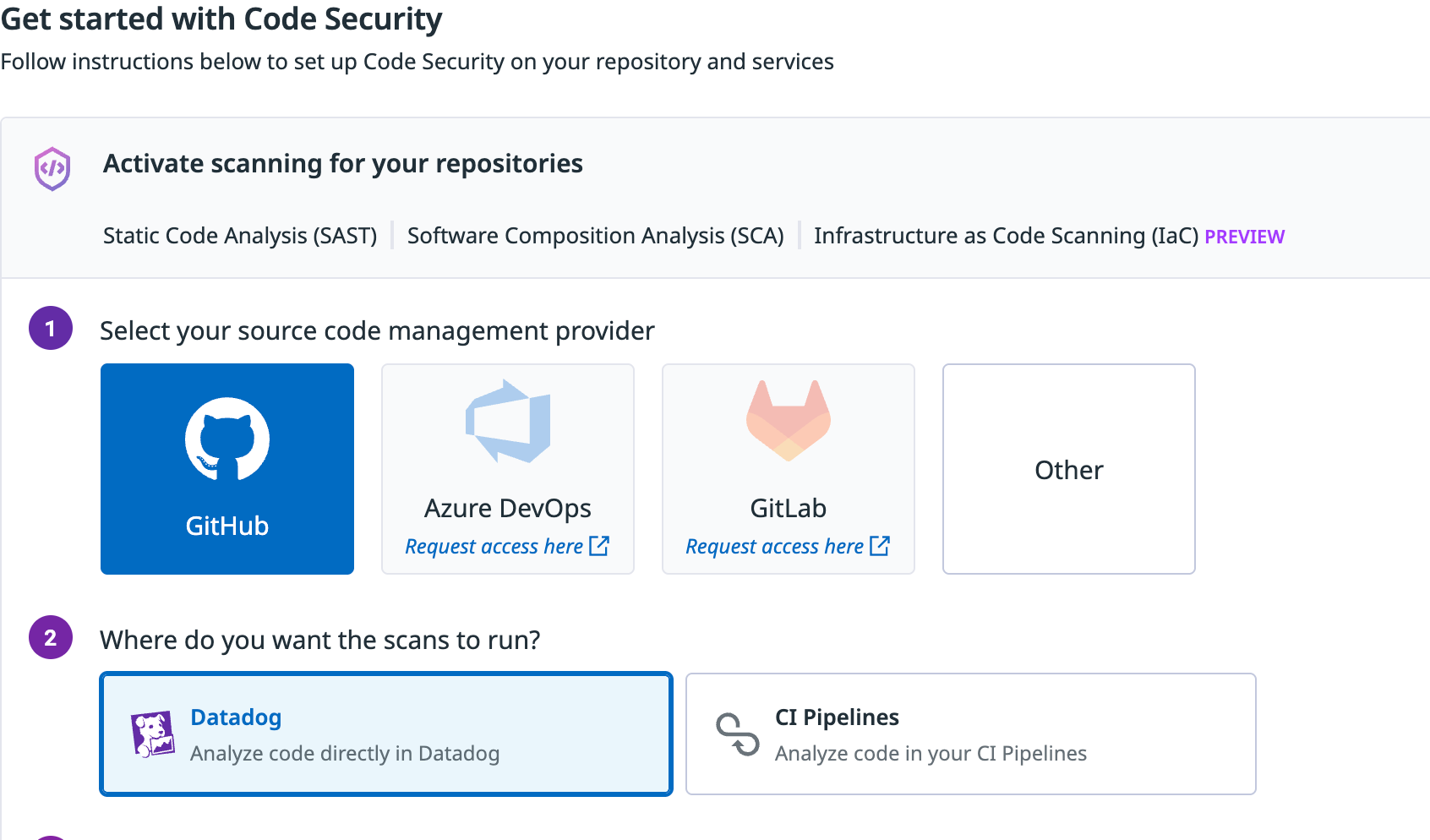
- Click the blue + Create GitHub App button.
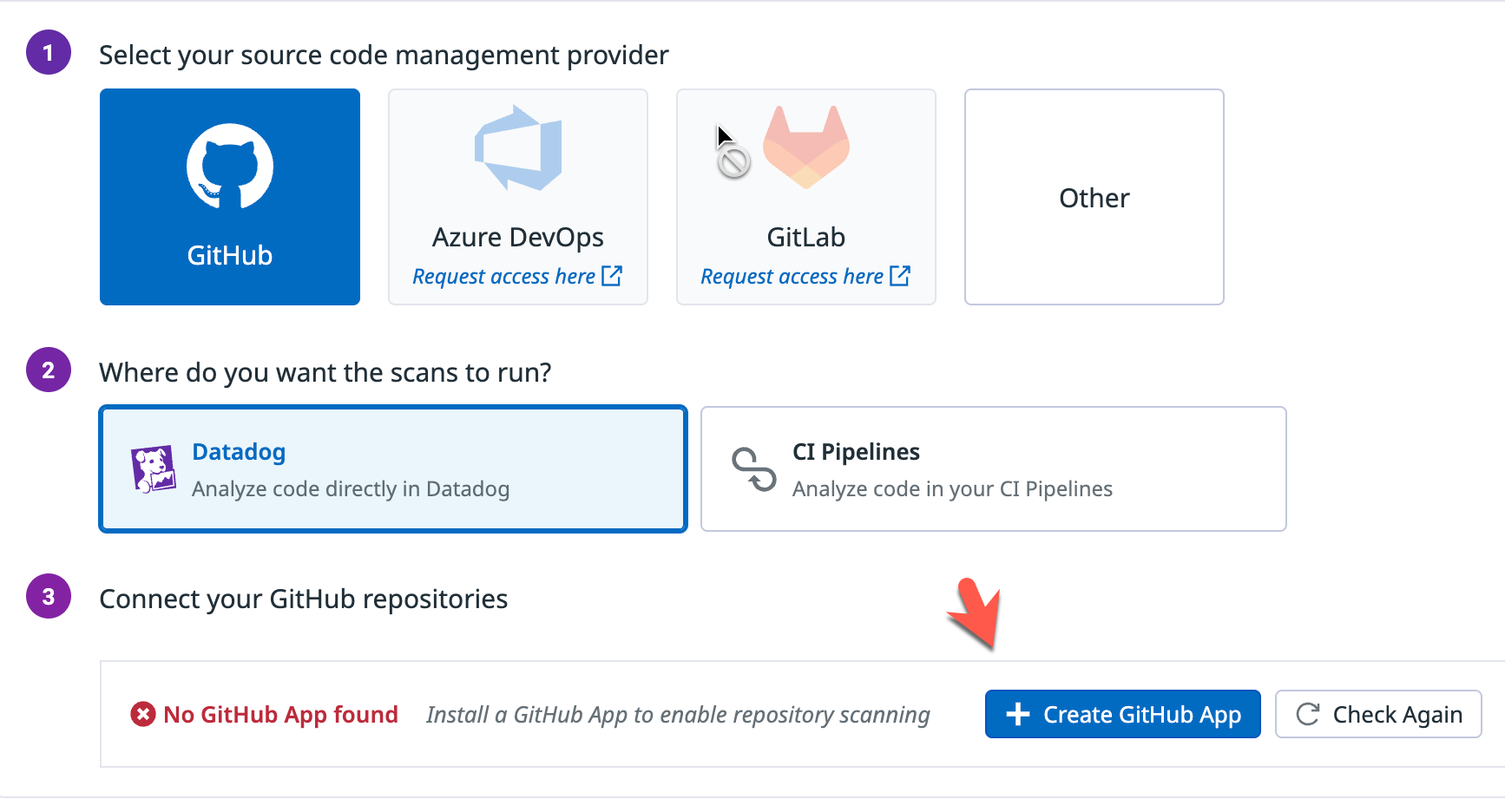
- Click the blue + Create GitHub App button. again and ensure you use the appropriate account type (organization or personal).
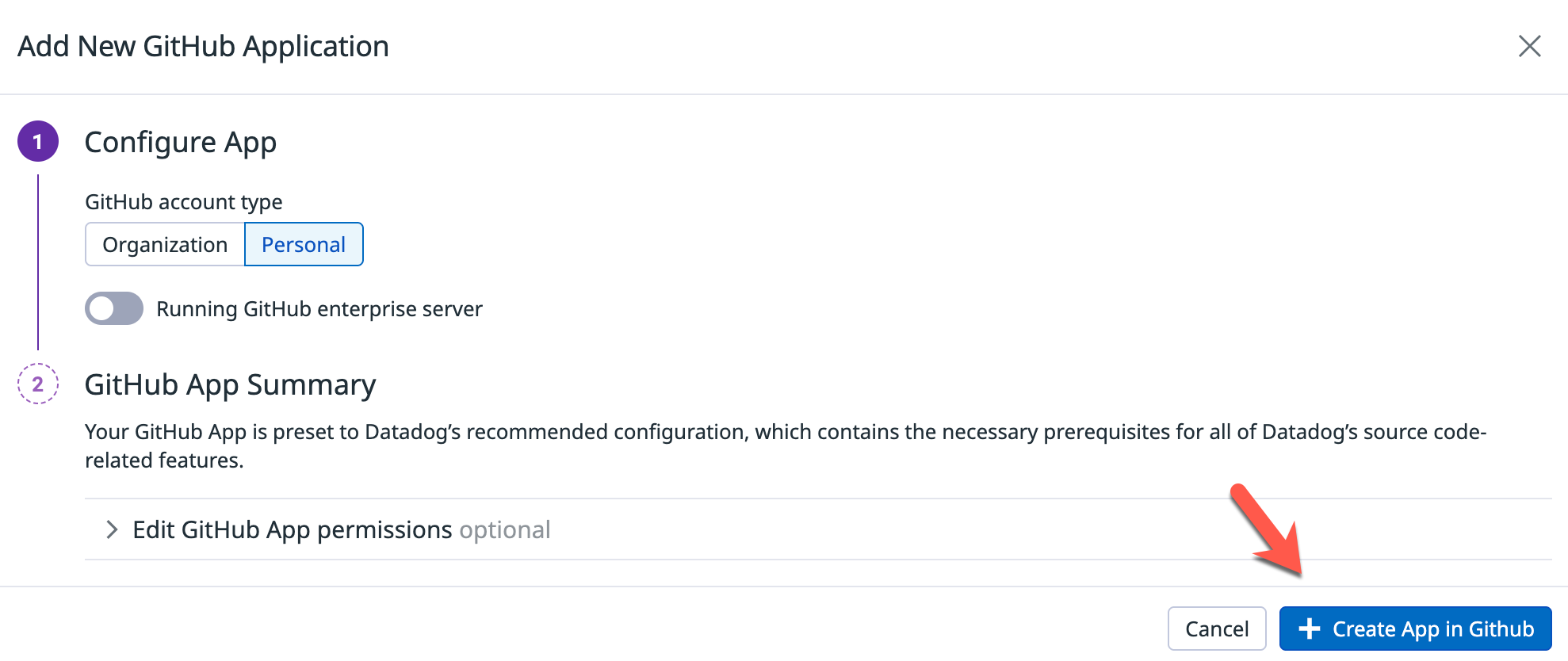
- Once you click the blue + Create App in GitHub button, it'll bring you to your GitHub account (if you're already signed in) and you'll create an app that gives Datadog access to look at your repos.
From a security perspective, it's best to choose specific repositories instead of giving Datadog access to everything.
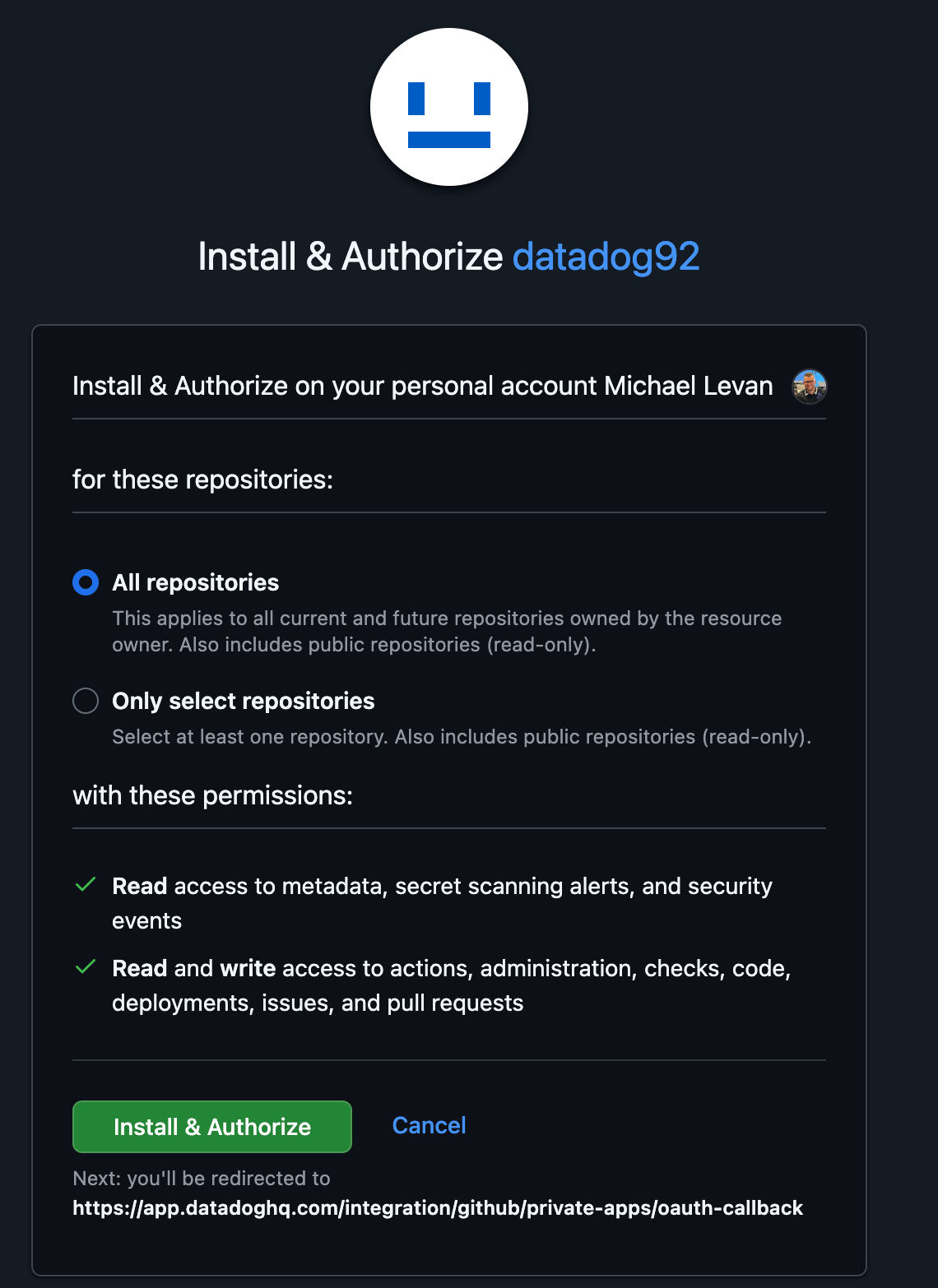
After you select your repos, you may have to click the Security pane again in Datadog and click the Enable button for SAST. It doesn't seem to bring you back to the appropriate page to enable the scanning once you give access to your GitHub repos.
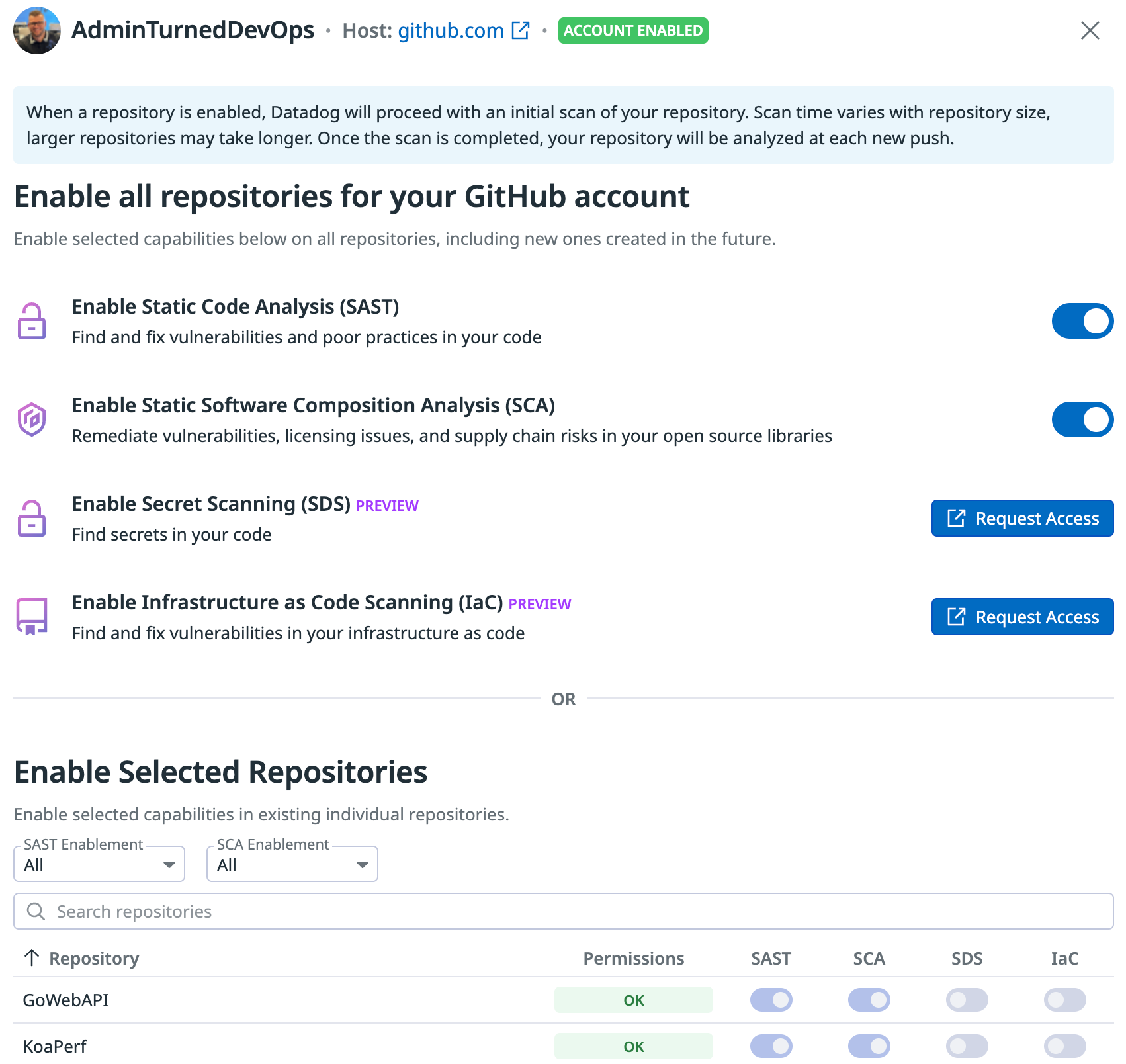
- Now that the repos are added in Datadog, you can toggle SAST and SCA on.
The end result will show the configurations for SAST and SCA are now enabled.
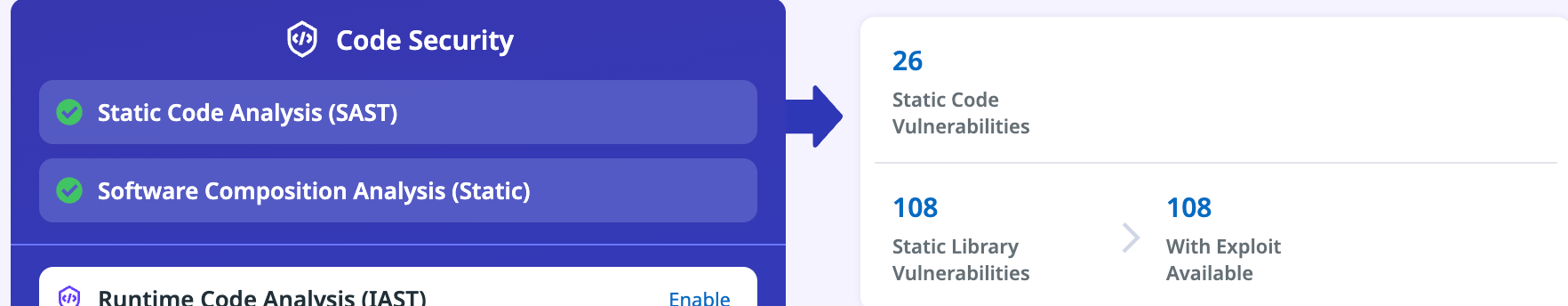
Scanning Code
In the previous section, you enabled SAST and SCA within Data. Now that it's enabled, you can begin scanning. Luckily, it's pretty straightforward. There's nothing you need to do other than go to the panel where the potential vulnerabilities exist.
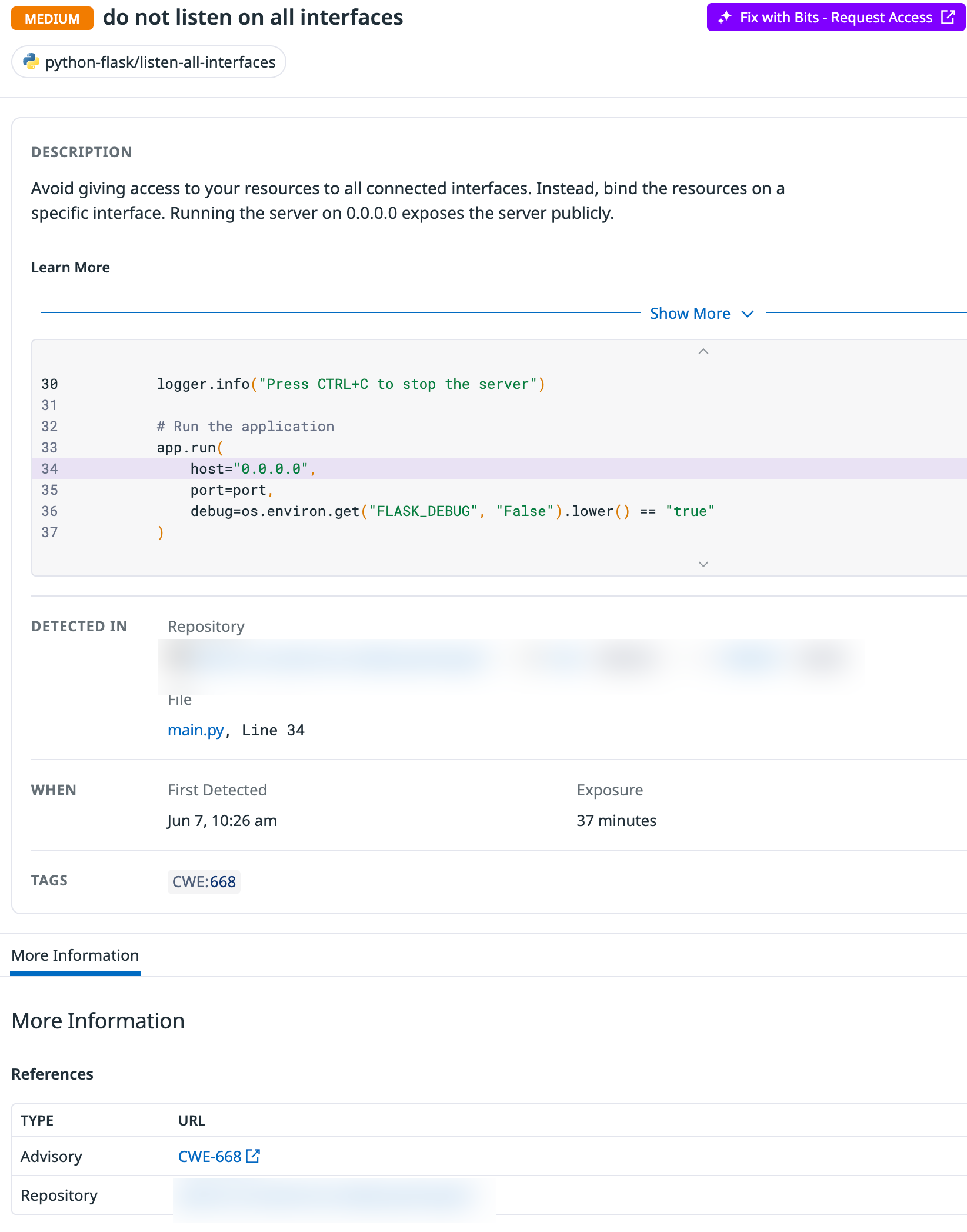
- Within the Security pane via Datadog, you should see some vulnerabilities showing up (it includes low and medium as well, so there is most likely something available to click).
When you click on one of the vulnerabilities, you may not see anything pop up right away. It takes a few minutes for all of the vulnerabilities to get loaded into Datadog.
You can now see the vulnerabilities within your environment.
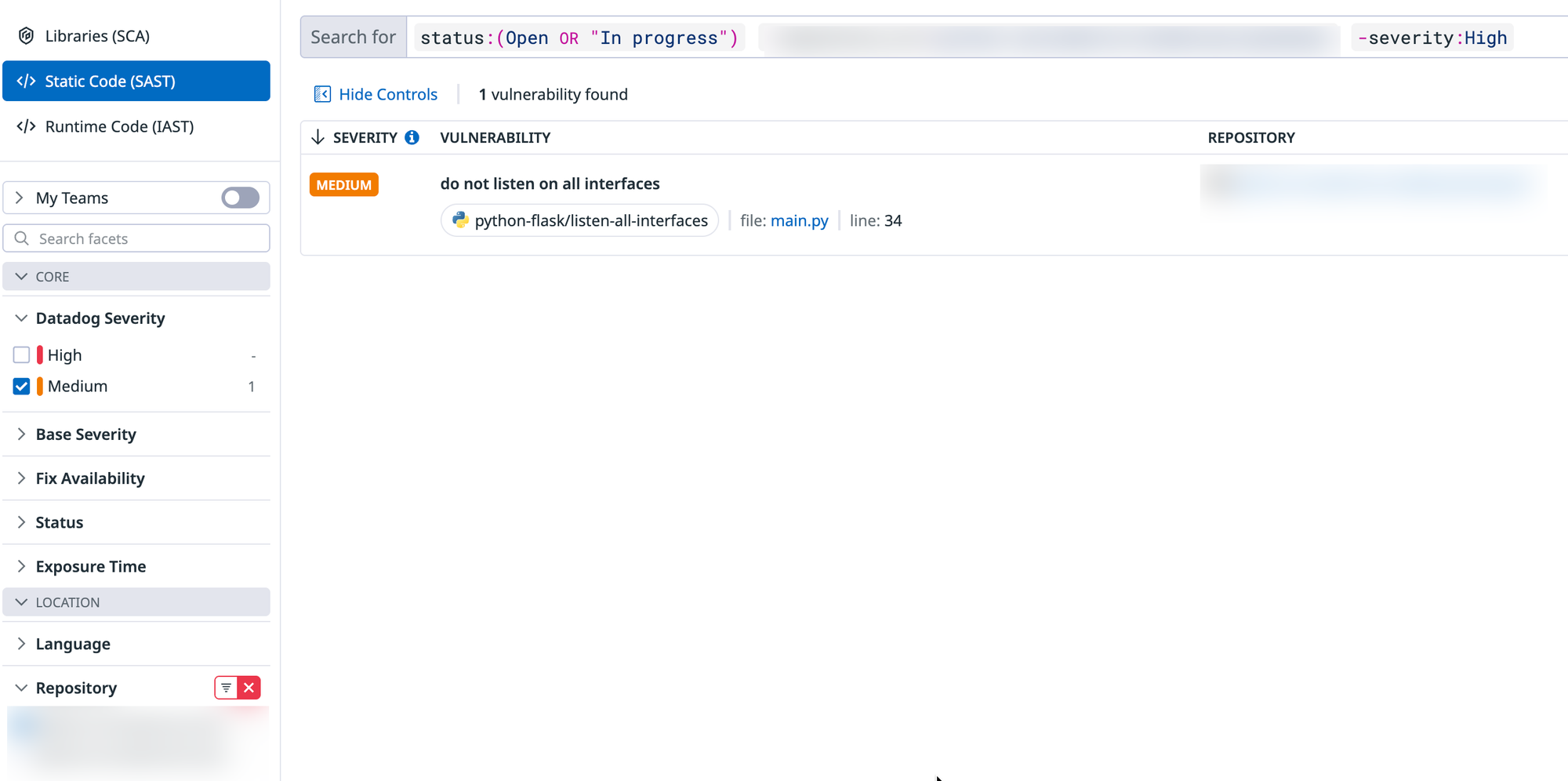
- Click on one of the vulnerabilities and it will give you a full breakdown of the vulnerability, how to fix it, and the reference documentation for said vulnerability.
Congrats! You've successfully implemented a few of the Datadog AppSec configurations for application code.




Comments ()